
TCP, HTTP and SPDY Deep Dive
TCP, HTTP and SPDY Deep Dive, available at Free

Internet Safety: Guide to Online Privacy and Security
Internet Safety: Guide to Online Privacy and Security, available at Free
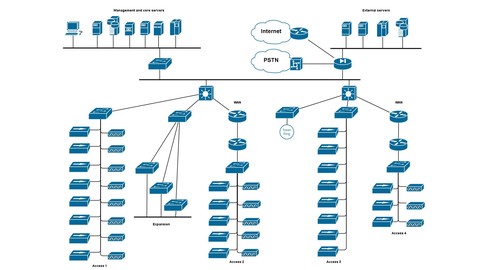
Introduction to Networking (Quick Course)
Introduction to Networking (Quick Course), available at Free

Responsible Machine Learning
Responsible Machine Learning, available at Free

parameter tampering | bug bounty hunting
parameter tampering | bug bounty hunting, available at Free

Cryptography & Security: Protect Data from Cyber Threats
Cryptography & Security: Protect Data from Cyber Threats, available at Free

Cybersecurity for Small and Medium size business
Cybersecurity for Small and Medium size business, available at Free

Learning SSH and Putty for Linux/Unix based systems
Learning SSH and Putty for Linux/Unix based systems, available at Free

Information Disclosure Mastery: Hands-on from Zero to Hero!
Information Disclosure Mastery: Hands-on from Zero to Hero!, available at Free

